Top Process Mining Use Cases for Cybersecurity
The practice isn’t new, but the application of process mining to cyber - is
Gutsy Staff | January 4, 2024

Security teams are constantly improving their security outcomes and protecting sensitive information, yet cybersecurity threats persist with a new breach seemingly making headlines every week. This is why we expect process mining to transform how enterprises look at cybersecurity solutions in 2024.
Process mining for threat detection focuses on studying and enhancing how a business already operates. Dedicated tools built to integrate into existing systems analyze event logs and data sources to find issues and risks in an organization’s security processes. These tools then use algorithms and machine learning to extract insights.
Once a company knows what works, they can start to fix what doesn’t.
Here are the anticipated top process mining use cases in cyber in 2024:
- Externally reported vulnerabilities
- Transforming auditing
- Compliance monitoring
- User off-boarding
- Business email compromise
- Fraud detection
Externally Reported Vulnerabilities
One important way to use process mining for cybersecurity is to find vulnerabilities that others have reported. With the rise of cyber attacks, businesses are constantly at risk of being targeted by hackers. Companies can use process mining to study their processes and find weaknesses that might be taken advantage of by outside threats.
For example, if a company's process for handling sensitive customer data is not secure, it could be easily exploited. Process mining can find these weaknesses and assist businesses in securing their procedures and safeguarding sensitive information.
Transform Auditing
Right now, auditing is often a high cost, low value activity which stands to be transformed through process mining. Streamlining the auditing process will be especially useful for businesses that need to comply with strict regulations and standards. These include the Health Insurance Portability and Accountability Act of 1996 (HIPAA) or the European Union’s General Data Protection Regulation (GDPR). However, all companies can benefit from ensuring their processes are in line with any regional, or industry-specific, regulatory and compliance guidelines.
To be highly effective at improving auditing for enterprises, a security process mining tool needs to provide a dashboard or roadmap of how security functions are really working. Metrics to keep an eye on include conformance ratios so teams can see, at a glance, if their process is running as expected.
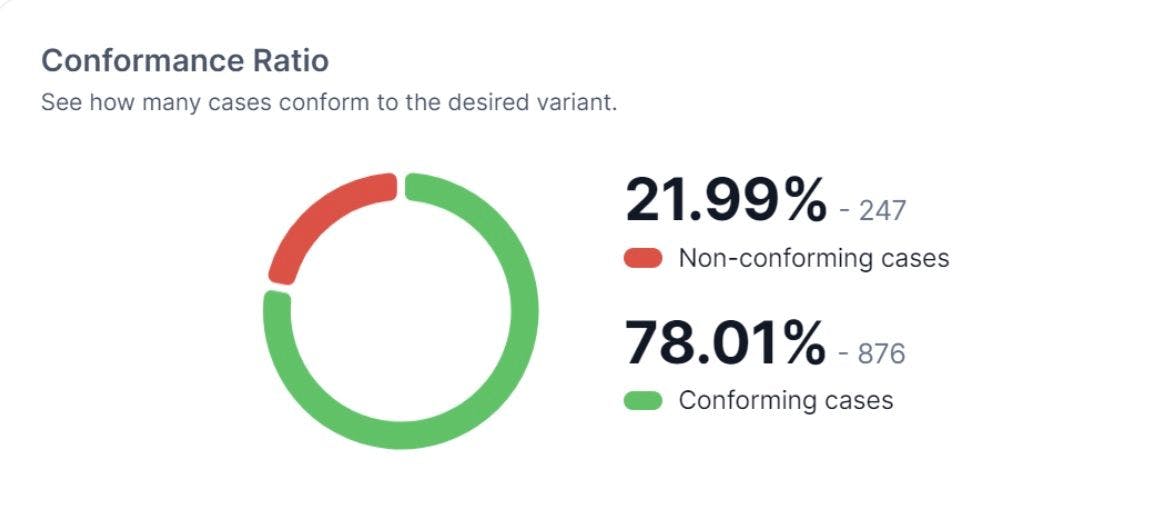
A collaborative platform that plugs into all systems involved in the audit scope. This way it can mine for historical data about the events the systems have performed, and automatically correlate the data. This collaborative aspect is especially important for collapsing the amount of lag time between collecting data and driving real changes to reduce risk across an organization.
Compliance monitoring
HIPAA, GDPR and the California Consumer Privacy Act (CCPA) are fueling the prioritization of companies to comply with the growing number of data privacy regulations.
Process mining can monitor data flows and identify any potential violations to help businesses ensure compliance.
By analyzing data logs and user behavior, process mining can detect any unauthorized access to sensitive information and flag it for further investigation. This can help businesses avoid costly fines and maintain their reputation as a trustworthy organization.
User Off-boarding
When an employee leaves a company, one misstep can put sensitive information in the wrong hands. This is especially true when the user has heightened privileges, such as being an administrator or root user. However, the off-boarding process can be time-consuming and, despite the best intentions, prone to errors.
Consider an example of an organization requiring the removal of access to cloud service providers as part of their off-boarding process for dev team members. In most cases, the organization removes access to the employee from both dev and production accounts.
However, if a process flaw results in access only being removed from one, but not both, accounts, the company is exposed to the risk of a former employee leaking sensitive information. This security risk can't be tracked to a lack of tools. It is the result of a failed, and unchecked off-boarding process.
Business Email Compromise (BEC)
Business email compromise (BEC) is a type of cyber attack where hackers impersonate a company's CEO or other high-level executives to trick employees into transferring money or sensitive information. This type of attack is becoming increasingly common.
Process mining is a useful tool for finding patterns and unusual things in email communication. For example, it can help identify strange email addresses or requests for sensitive information.
This can help businesses detect and prevent BEC attacks before they cause any damage.
Fraud Detection
The impact of fraud on a company's bottom line can't be overstated. However, businesses that leverage process mining’s abilities to automate fraud detection and prevention through data log analysis are better equipping their security teams to spot suspicious activity sooner than traditional analysis methods alone.
By monitoring user behavior and identifying any deviations from the norm, process mining can help businesses take proactive measures to prevent fraud and protect their financial assets.
How Gutsy can help
By incorporating process mining into their security strategy, security teams can stay one step ahead of cyber threats.
We recently discussed other benefits of process mining for security leaders specifically, and how the practice accelerates business outcomes in this free webcast, “How to Level Up Your Security Governance with Process Mining.”