What is Gutsy?
Gutsy is a security process fabric that unifies intel from across your vulnerability management lifecycle.
Connect to all the systems you're already using. Find and fix vulnerabilities, from scanners to ticketing systems to code repos and cloud platforms, and use process mining to correlate activity across them.
Visualize root cause detection to remediation, code fixes to deployments, and ask Gutsy AI hard questions about this complex data.
For the first time, you can see the most critical risks and track the processes to resolve them.
What is a Security Process Fabric?
Gutsy gives you a bird's eye view of all your security related processes, illustrating each step and hand off in every execution.
Gutsy automatically connects to all the systems you're already using, continuously gathers events from them as they happen, and automatically correlates complex workflows across them.
Gutsy Is Built To Go Beyond Vulnerability Management
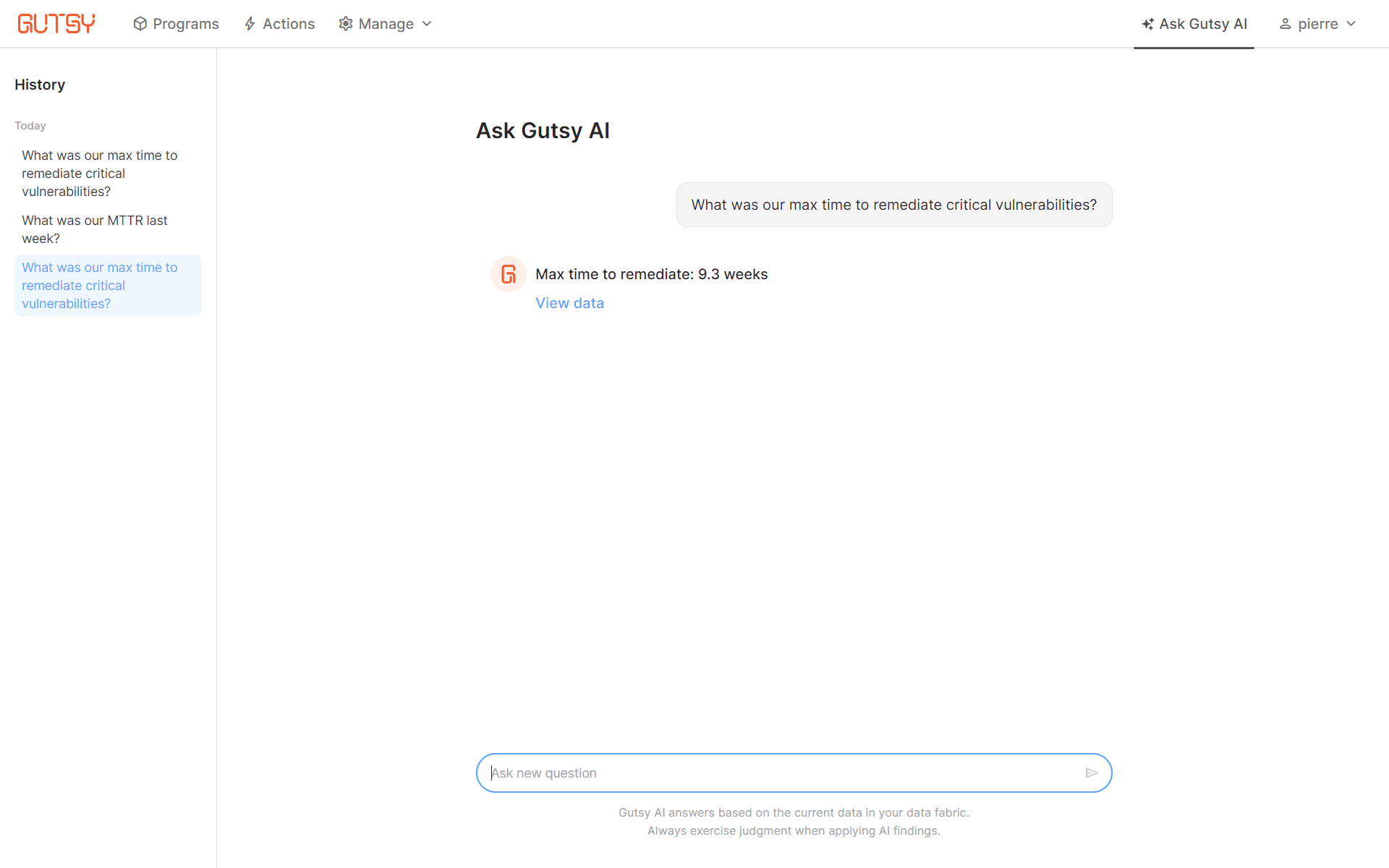
Gutsy AI makes it easy to analyze complex vulnerability data
- Generative AI built specifically for vulnerability management
- Entirely private architecture with no data sent to 3rd parties
- Quickly generate customized views and reports
- Quickly slice and prioritize complex vulnerability data sets

Dashboards align teams and service providers to drive down MTTR of critical CVEs
- Consistent and continuous visibility that replaces manual spreadsheets
- Customize goal-setting, performance metrics and streamline reporting
- Communicate progress across your entire program regardless of toolsets

Blueprints map out your end-to-end path to successful remediation
- Define how you want to follow a process for remediating vulnerabilities in each of your environments
- Adjust blueprints based on best practices and measure adherence over time
- Automatically take action when a blueprint isn’t followed

Actions establish guardrails for your vulnerability management processes
- Attach actions to any vulnerability management process
- Set enforceable KPIs for each step with clear deadlines for resolution
- Proactively get notified - and take action - when remediation doesn’t meet SLA

Process Explorer is strace for your vulnerability management process
- Understand why CVEs persist: whether due to a missed code fix, incomplete deployment, or other issue
- Get a data-based view of which manual steps are draining your resources, and identify opportunities for automation
Trust Center


Product Architecture
Work with Your Existing Detection Tools
Data is mined directly from your cloud services into Gutsy, and you can deploy a self-hosted collector for systems behind your firewall.
It is a SaaS service built for security and privacy with SOC2 and ISO 27001 accreditation.
Each customer tenant runs as an isolated container in the customer’s specified region. Our security process fabric doesn't require any agents to deploy or software to develop and offers familiar, user-driven collaboration capabilities with role-based access, giving full control over who has access to what process data.
Cloud delivered SaaS product
Data is mined directly from your cloud providers into Gutsy and you can deploy a self-hosted collector for systems behind your firewall
Deployed in the region you choose
Familiar, user driven, collaboration capabilities with full control over who has access to what process data
Native support for major identity providers for single sign-on access
Wide and ever growing integration library covering both security and non-security tools like HR and ticketing systems
Ready to Learn More?
Gutsy gives you a 720° view of your vulnerability management program so you can understand it end-to-end, from discovery to triage to testing.